Norton Smart Firewall: How It Works and Why It’s Safer Than a Traditional Firewall in 2025

Why Norton Smart Firewall Remains Essential in 2025 In 2025, cyberattacks evolved far beyond classic viruses. Today’s attackers use privilege escalation, fileless attacks that leave no trace on disk, code injection, exploitation of open ports, lateral movement inside networks and remote access hidden within legitimate connections. Against these threats, a traditional firewall is not enough. […]
How to Use Norton Password Manager to Protect All Your Passwords in 2025
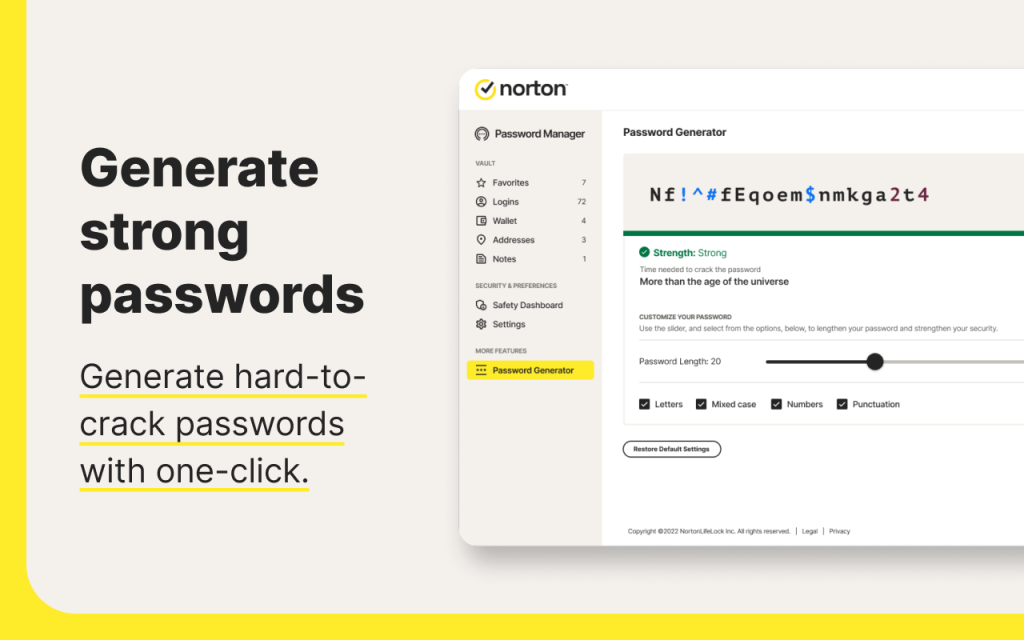
Why Norton Password Manager Is Essential in 2025 Norton Password Manager has become one of the most widely used tools for securely managing passwords in 2025. With the rise of data breaches, brute-force attacks, identity theft and credentials leaked on the dark web, memorizing passwords or saving them in the browser is no longer enough. […]
Complete guide to installing Norton on Windows, Mac, Android and iOS without errors

Installing Norton in 2025 is much easier than it used to be, but each operating system still has its own requirements, permissions and critical steps that, if not configured correctly, can leave your protection incomplete. Many users experience activation errors, compatibility issues or disabled features without even realizing it. This guide explains in detail how […]
Norton 360: what it really includes and which plan is ideal for your business or personal use
Norton 360 has become one of the most complete cybersecurity suites available today, yet online information is often confusing or incomplete. Between antivirus, smart firewall, VPN, cloud backup, parental controls and dark web monitoring, it’s not always clear what each plan includes or which one is actually worth paying for. This guide breaks down the […]
Cloud Protection: How Norton Adapts to Remote Work and Hybrid Environments
In recent years, remote work and hybrid environments have become a reality for companies of all sizes. Flexibility and productivity have increased, but so have cybersecurity risks. With employees connecting from home networks, mobile devices, and cloud applications, attack surfaces have multiplied. In this context, having reliable protection adapted to the new way of working […]
The browsing evolution continues with the AI browser Norton Neo

The browsing evolution continues with the AI browser Norton Neo As AI transforms how we interact with the web, it’s clear we need a new kind of browser. Enter Norton Neo: an AI-native browser built for the future. The internet browser has come a long way from static pages and dial-up tones. What started as […]
What is an IP address?
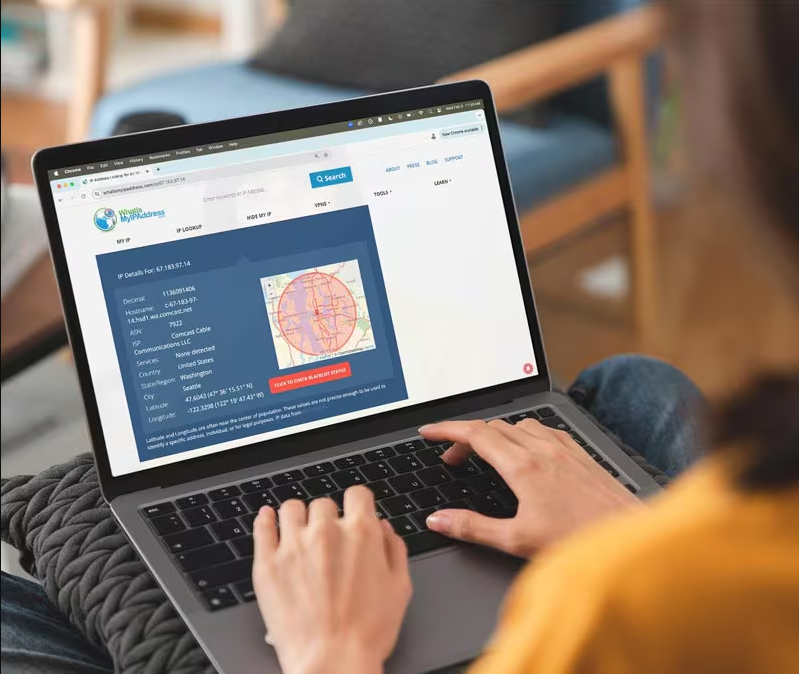
What is an IP address? Your IP address is like your digital home address. It lets your devices, like your computer or phone, connect online for things like browsing, shopping, and messaging. Learn how IP addresses work, the different types, and how Norton VPN can help shield your IP from tracking, surveillance, and online threats. […]
How to remove a virus from an Android phone in 6 steps
How to remove a virus from an Android phone in 6 steps Is your phone slowing down or overheating? Unusual behavior could be a sign you have a virus. Learn how to remove viruses from your Android and discover how Norton can help stop scam attempts and malware from stealing your information or money. Threat […]
Ransomware statistics: Facts and trends for 2025

Ransomware statistics: Facts and trends for 2025 Ransomware is an ever-growing threat to businesses, organizations, and individuals everywhere. The more you know about this cyber-menace, the better protected you are. Learn about some of the most alarming ransomware statistics, and defend against ransomware attacks and other digital threats with a state-of-the-art Cyber Safety tool. Ransomware is […]
Top 5 social media scams

Top 5 social media scams Los sitios de redes sociales como Twitter y Facebook tienen un lado oscuro. Las solicitudes de phishing son una táctica común de los ciberdelincuentes. Tenga cuidado de no hacer clic a ciegas en URL acortadas. Compruebe su protección antivirus y anti-spyware. We’re wired to be social creatures, and sites like Twitter and […]
